Hardware MFA tokens for Office 365 / Azure cloud Multi-factor authentication - Legacy UI
How to use Token2 programmable tokens with Azure MFA
Token2 programmable tokens are a "drop-in" replacement of mobile applications such as Google Authenticator or Token2 Mobile OTP. If you are using Office 365 with Azure MFA protection enabled, you can use our programmable tokens as an alternative to mobile application method by following the instructions below. Please note that this requires no administrative priveledges and any user can benefit from this method. The only prerequisite is an NFC-enabled device running one of our apps.
Step1. Install one of the burner apps and make sure your token is accessible via NFC.
I.e. you can test NFC access by "get info" button of the app: push the button on the device and hold it close to the NFC antenna of your device (on the phones it is usually below the camera on the back). Then on the Burner App, touch the "get OTP" or "get Info" button. The OTP shown on the app should match the one displayed on the token. Be aware of NFC stability issues with some devices described here.Step 2. Enable or reconfigure Authenticator app on your Office 365 account
Navigate to MFA setup page and make sure you have Authenticator app setting enabled. 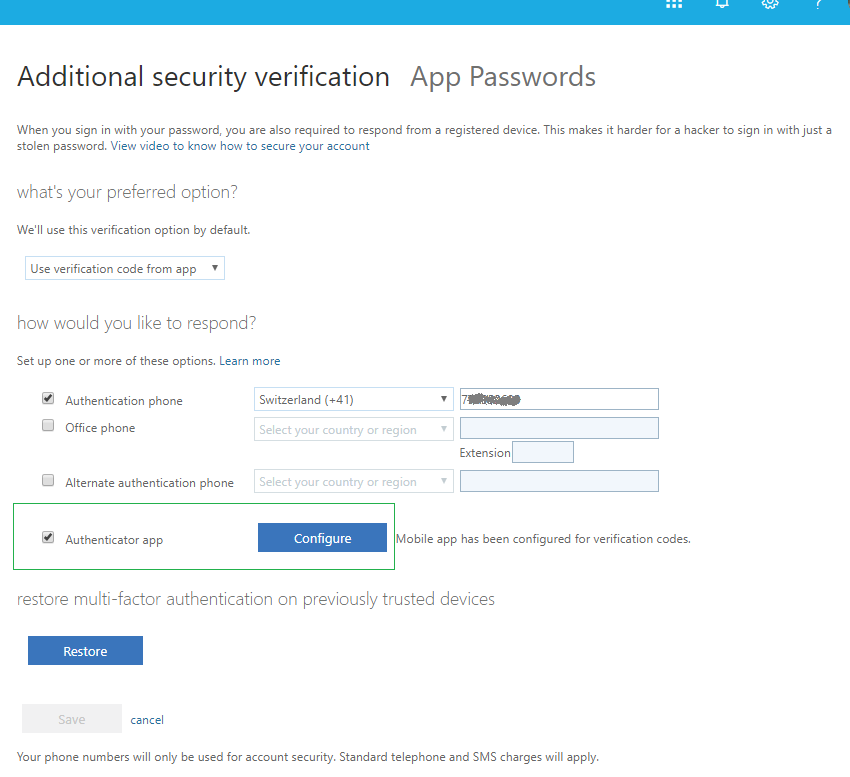
Click on the "Configure" button. A QR code will be shown on the pop-up page. Click on "Configure app without notifications" link in order to switch from the default proprietary QR code format (phonefactor) to standards-based TOTP profile.
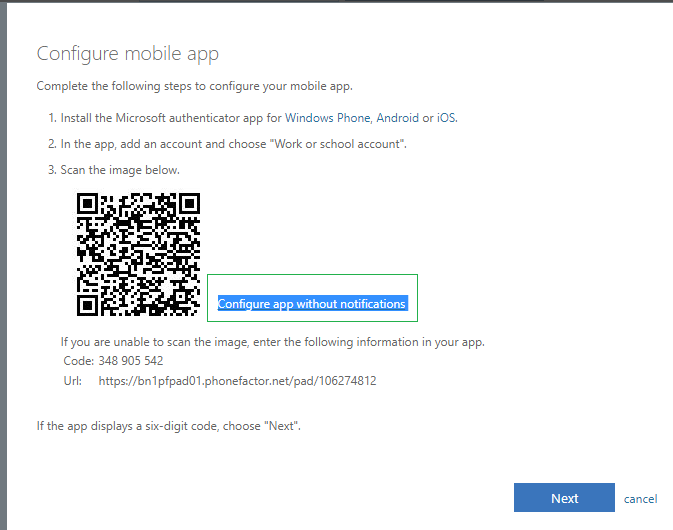
Keep this window open and proceed to Step 3 on your mobile device.
Step 3. Burn the token with Token2 Burner App
Launch Token2 Burner App on your device. Click on Scan QR button and scan the QR code shown on the configuration page as described in the previous step or enter the seed manually or copy&paste from the screen. Then, push the button on the token and hold it close to the NFC antenna of your device . Click on "burn seed" button. The app should show "burn seed process succeeded" message if the process is successfully completed.
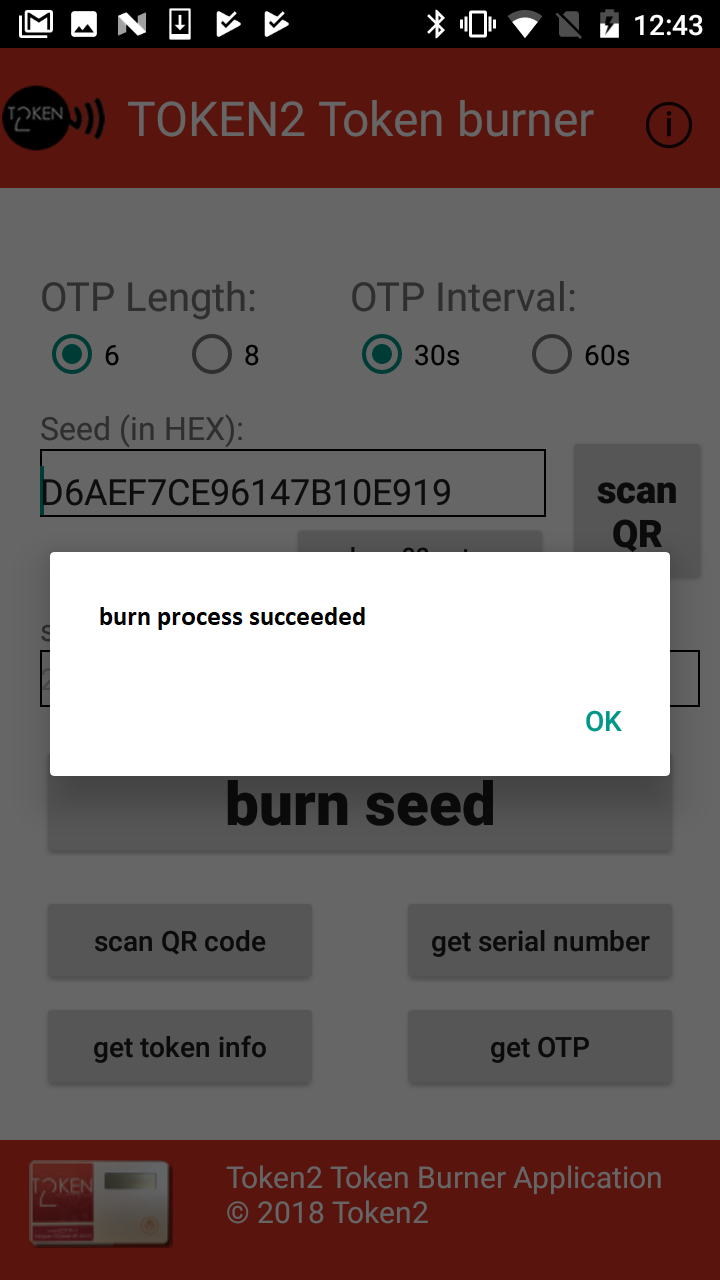
Step 4. Verify the token and complete the enrollment
After the burn process is completed, click Next and proceed with OTP verification. To verify the OTP, click on "Verify Now" button, and on the next step, enter the OTP code displayed on your token device.
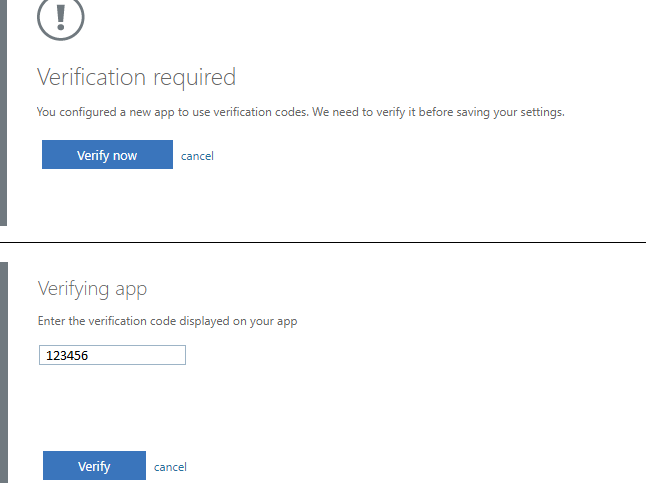
Complete the process by clicking on "Verify".
Frequently asked questions
- Q. Do I need tenant admin rights in order to use hardware tokens with cloud-hosted Azure MFA?
- A. Not for cloud Azure MFA. Token2 programmable tokens fully emulate mobile apps, so it can be enabled (and disabled) by end users themselves.
- Q. Can the miniOTP-1 token be reused for another user (i.e. if the previous owner left the company)?
- A. Yes. the miniOTP-1 tokens are reprogrammable for an unlimited number of times. So the steps described above can be repeated for any user using any miniOTP-1 device (even previously owned).
- Q. Why does the burner app crash when I scan the QR code?
- A. The QR code shown by default on this page is in Microsoft's proprietary format (phonefactor protocol) and is not compatible with the QR reader component of our app. Please make sure you switch to "Configure app without notifications" mode before scanning the QR code.
- Q. Can I use both hardware and software token simultaneously?
- A. Yes, as long as "Configure app without notifications" option is maintained. When you see the QR code after clicking "Configure app without notifications" you can scan it using a mobile app (such as Google Authenticator or Token2 Mobile OTP) before continuing with burning the seed on the programmable token.
- Q. Can other types of hardware tokens (for example c200) be used with Azure MFA?
- A. Onprem hosted MFA server (Azure MFA Server) supports any TOTP tokens, however, cloud Azure MFA is currently in public preview. Refer to this blog post for more details. Worth mentioning that the same tokens can be easily reused even after this feature becomes available.
- Q. Is there support for time drift and time skew of the hardware tokens in Office 365 with Azure MFA?
- A. We have tested the accepted skew with Azure MFA using our TOTP Toolset and discovered that the allowed skew around 900 seconds (15 x 30-second steps in each direction) which means that no adjustment is needed. If you still need the time to be accurate, you can use our programmable hardware tokens with time sync feature
- Q. Why a hardware token more secure than other methods such as mobile apps, texts or voice calls?
- A. Physical hardware tokens are a much more secure protection a user can currently have. A separate, isolated device generates OTP codes fully offline without any need for Internet or any other network access. There is no potential way for attacker access nor infect the device or intercept the generated one-time passwords. In case a hardware token is lost or stolen the user will notice it right away. This is not the case with a mobile app running on an infected mobile device or a text message intercepted at the GSM network level; with these methods, the victim may not even be aware of the attack at all.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
