Token2 TOTPRadius Virtual appliance
download purchase integration guides
 Token2 TOTPRadius provides the RADIUS RFC-2865 for TOTP RFC-6238 based authentication. With TOTPRadius you can integrate a large variety of third-party products and systems with multi-factor authentication. A number of enterprise products and services like VPNs, Citrix XenApp/XenDesktop, VMWare View and many others provide support for RADIUS servers to validate the second factor of user authentications. Additionally, TOTPRadius appliance is providing RESTful API for second-factor authentication and enrolment (including self-service enrolment where possible). This allows implementing a fully on-premises secure and user-friendly two-factor authentication supporting RADIUS and LDAP protocols together with HTTP API with one appliance. TOTPRadius supports OTP-only authentication based on RFC-6238 algorithm (TOTP: Time-Based One-Time Password Algorithm), Local password + OTP combined authentication as well as LDAP+OTP combined authentication. It provides a web-based administration panel and an HTTPS REST-based API service designed to enable users' self-enrollment.
Token2 TOTPRadius provides the RADIUS RFC-2865 for TOTP RFC-6238 based authentication. With TOTPRadius you can integrate a large variety of third-party products and systems with multi-factor authentication. A number of enterprise products and services like VPNs, Citrix XenApp/XenDesktop, VMWare View and many others provide support for RADIUS servers to validate the second factor of user authentications. Additionally, TOTPRadius appliance is providing RESTful API for second-factor authentication and enrolment (including self-service enrolment where possible). This allows implementing a fully on-premises secure and user-friendly two-factor authentication supporting RADIUS and LDAP protocols together with HTTP API with one appliance. TOTPRadius supports OTP-only authentication based on RFC-6238 algorithm (TOTP: Time-Based One-Time Password Algorithm), Local password + OTP combined authentication as well as LDAP+OTP combined authentication. It provides a web-based administration panel and an HTTPS REST-based API service designed to enable users' self-enrollment. VPN Portal is a subcomponent of TOTPRadius appliance and is required to implement several features, such as LDAP-based self-service enrollment, FIDO2/Passwordless or Azure AD (Microsoft Entra ID) Oauth2/SSO VPN access. To ensure the security of the VPN Portal is at the highest level, we have contracted an independent security company, SySS GmbH , which has conducted the penetration testing and produced a security certificate available below. The TOTPRadius VPN Portal component is currently labeled as "Certified Website - Approved Security" by SySS Gmbh.
VPN Portal is a subcomponent of TOTPRadius appliance and is required to implement several features, such as LDAP-based self-service enrollment, FIDO2/Passwordless or Azure AD (Microsoft Entra ID) Oauth2/SSO VPN access. To ensure the security of the VPN Portal is at the highest level, we have contracted an independent security company, SySS GmbH , which has conducted the penetration testing and produced a security certificate available below. The TOTPRadius VPN Portal component is currently labeled as "Certified Website - Approved Security" by SySS Gmbh.
Self-enrollment using RESTFul API
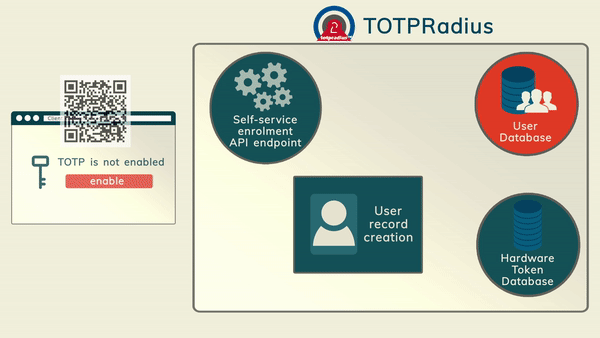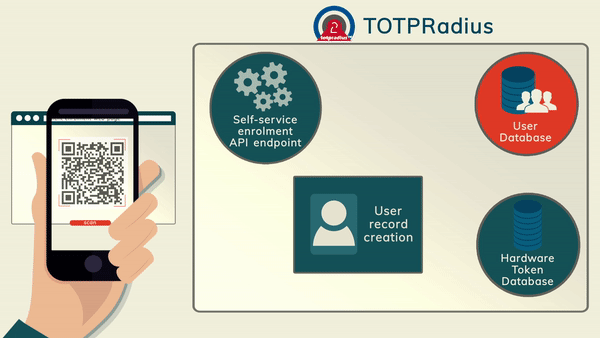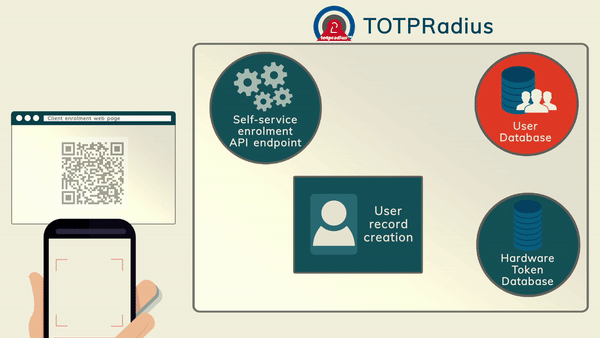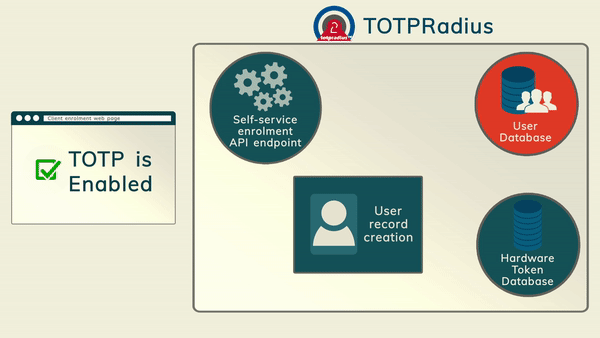 The main advantage of TOTPRadius is the RESTFul API that allows users to self-enrol with their software tokens such as Google Authenticator and Token2 Mobile OTP.
An example of such an integration is a self-enrollment mechanism with Citrix Netscaler/StoreFront. The integration can be done by installing our Storefront integration package and adding a new RADIUS authentication server on the Netscaler. It usually takes not more than five minutes to implement. Refer to Citrix integration manual for more details.
The main advantage of TOTPRadius is the RESTFul API that allows users to self-enrol with their software tokens such as Google Authenticator and Token2 Mobile OTP.
An example of such an integration is a self-enrollment mechanism with Citrix Netscaler/StoreFront. The integration can be done by installing our Storefront integration package and adding a new RADIUS authentication server on the Netscaler. It usually takes not more than five minutes to implement. Refer to Citrix integration manual for more details.
Self-enrollment using LDAP Enroll web interface
You can configure TOTPRadius to allow users to log in without second factor (e.g. using AD password only) for the first time and then navigate to TOTPRadius LDAP Enroll web interface (accessible only within your local network or VPN), where they can enrol the second factor independently. Administrators can also allow modifying (reenrolling) via LDAP Enroll web interface.LDAP Proxy
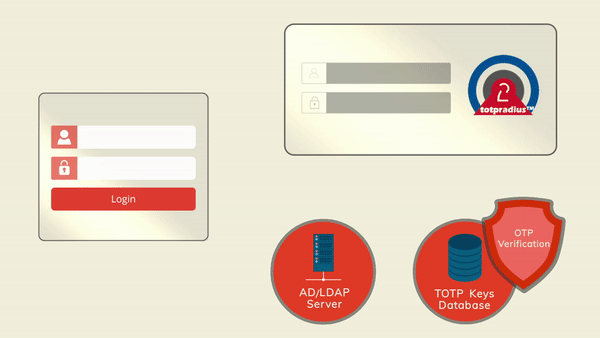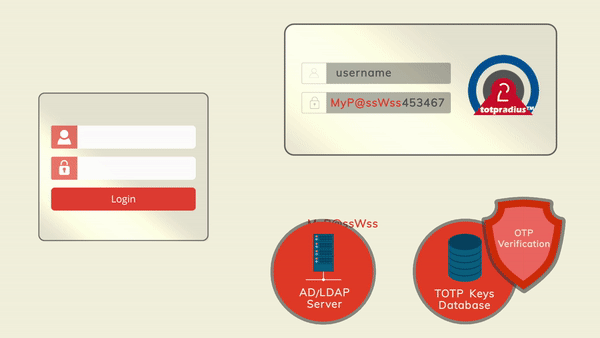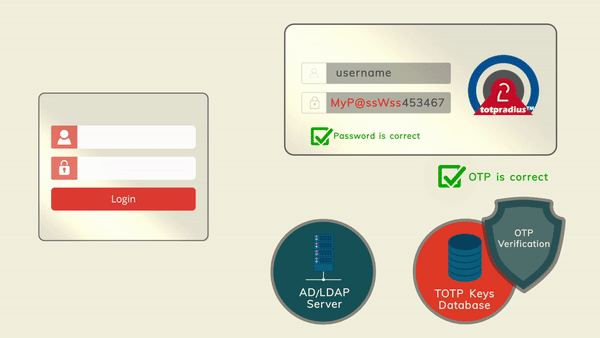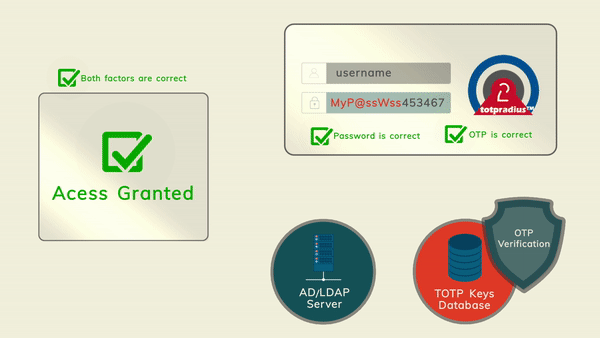 The principle behind LDAP Proxy mode is that users will provide their AD or LDAP password together with the one-time passwords in the password field. TOTPRadius will then parse the password, split it into two parts and authenticate the OTP and if correct will send the AD/LDAP password part further to the AD/LDAP server configured. The order of authentication is exactly as stated above, OTP is checked first and AD after OTP is confirmed correct; this is done in order to prevent account lockouts during brute force attacks. Enabling LDAP Proxy on your TOTPRadius appliance allows implementing two-factor authentication for systems that do not natively support it, such as Cisco Meraki VPN, Cisco WLC and many others
The principle behind LDAP Proxy mode is that users will provide their AD or LDAP password together with the one-time passwords in the password field. TOTPRadius will then parse the password, split it into two parts and authenticate the OTP and if correct will send the AD/LDAP password part further to the AD/LDAP server configured. The order of authentication is exactly as stated above, OTP is checked first and AD after OTP is confirmed correct; this is done in order to prevent account lockouts during brute force attacks. Enabling LDAP Proxy on your TOTPRadius appliance allows implementing two-factor authentication for systems that do not natively support it, such as Cisco Meraki VPN, Cisco WLC and many others
No LDAP? Use Azure AD (Microsoft Entra ID) Proxy
We are discovering more and more organizations moving to full cloud Azure AD (Microsoft Entra ID) implementation while keeping some services, such as VPN, on-premises. As the LDAP interface of Azure AD (Microsoft Entra ID) is not accessible directly, it was not possible to configure TOTPRadius to use Azure AD (Microsoft Entra ID) as its authentication source.
High availability and hardware token management
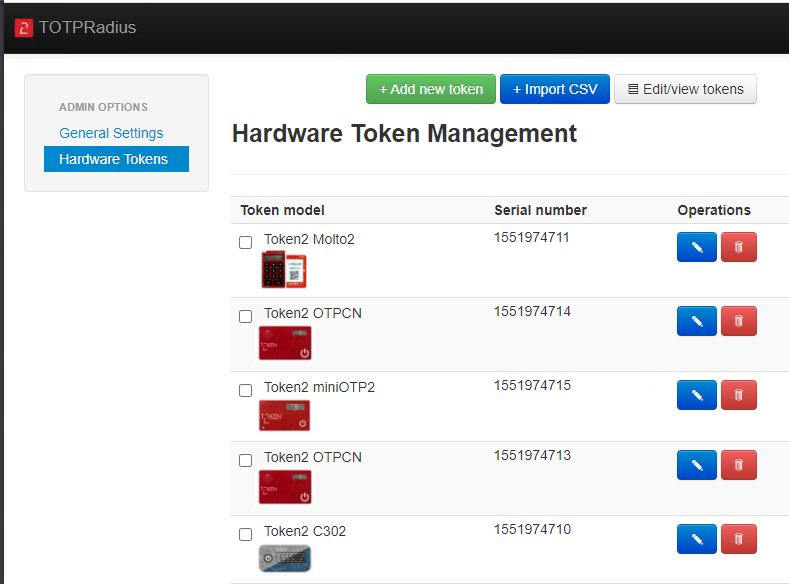 Starting from version 0.2.2 TOTPRadius appliances can be configured in high availability mode. Appliances in slave mode will only contain a read-only database will periodically synchronize with their master appliance via HTTPS REST API.
Starting from version 0.2.2 TOTPRadius appliances can be configured in high availability mode. Appliances in slave mode will only contain a read-only database will periodically synchronize with their master appliance via HTTPS REST API. Starting from version 0.2.4, TOTPRadius has a built-in management interface for hardware tokens. The hardware management tool allows adding and importing hardware token data, verify and adjust time drift using the virtual TOTP emulator and assign the hardware token to any user with a couple of clicks.
Download & install
▲
TOTPRadius is deployed as a software-based virtual appliance that runs on two hypervisors: VMWare ESXi and Microsoft Hyper-V. Upon request, virtual appliances for other hypervisors can be provided. It is free to use with up to 5 users. You need to obtain a license to increase the number of allowed users. You can download the appliance here
Changelog
[0.3.2] SHA256 TOTP Support (automatically detected if seed length >32 chars base32)[0.3.2] Strict OTP Mode (OTP cannot be used twice for the same user)
[0.3.2] Syslogs shown per user in the web admin
[0.3.1] SSH and Web Admin access limitations by IP
[0.3.1] API Changes (local user management)
[0.3.1] Azure AD (Microsoft Entra ID) MFA IP whitelist support
[0.3.1] Minor syslog message format improvements
[0.3.1] Operating system upgraded to Ubuntu 24 LTS.
[0.3] Endpoint IPs settings, now allows multiple endpoint ranges
[0.3] Hardware token management: uniqueness check, assigned token's serial number in user profile, search and other improvements
[0.3] T2VPN Interface update, now compatible with T2VPN NW.js client
[0.3] Licensing page update (license string can change only if more licenses are being added)
[0.3] Users clean-up function (for deleting users without second factor enabled after the initial grace period in bulk)
[0.2.9] Trusted client IP Configuration from which single factor authentication can be accepted
[0.2.9] RADIUS Dynamic attribute response based on AD Group membership
[0.2.9] Syslog option (Remote syslog server with a local copy)
[0.2.8] Additional API call for listing users (listusers , returns username and registration time in json)
[0.2.8] Backup and restore of the FIDO2 key registration
[0.2.8] Single factor mode improvement (allows both LDAP password and OTP if enabled)
[0.2.8] Allowing LDAP and Local Passwords mode coexistence
[0.2.8] Extra radius attributes
[0.2.8] Redesign of the private keys update web interface
[0.2.7] Appliance backup and restore features
[0.2.7] Import users using CSV file in Azure MFA file
[0.2.7] Azure AD (Microsoft Entra ID) Proxy mode feature
[0.2.7] Enforce HTTPS for Admin panel
[0.2.7] LDAP self-service interface localization option (+ de, fr, ru and tr)
[0.2.6] API Integration UI now shows the number of 'insecure' logins remaining
[0.2.6] Option to restrict hardware token assignment (one per user)
[0.2.6] Fallback mechanisms if the OTP submitted is incorrect: SMS via Twilio and/or Email via SendGrid
[0.2.5] LDAP-based self-service 2FA enrollment public facing web interface with an option to enroll hardware tokens
[0.2.5] LDAPS support with a possibility to upload the CA root certificate
[0.2.5] OAuth2.0-VPN Interface for Azure AD (Microsoft Entra ID) SSO
[0.2.5] FIDO-VPN Interface (with Passwordless support)
[0.2.5] Admin actions history
[0.2.5] Minor bug fixes
[0.2.4 RC1] Hardware token management and assignment feature added
[0.2.4 RC1] Non-ASCII Password allowed in LDAP Proxy mode
[0.2.4 RC1] Support for L10N of LDAP Enrollment page (EN and DE provided)
[0.2.4 RC1] Moved to Ubuntu 20 LTS
The installation and configuration are described in the documentation section.
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
09-12-2025
Framework ExpansionCard Enclosure for Token2 Keys
 Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
Framework laptops are all about modularity. The Framework ExpansionCard 3D-printable enclosure for Token2 PIN+ Type-C keys brings FIDO2 security directly into your device.
