TOTPRadius - RADIUS Dynamic attribute response based on AD Group membership
This can be configured in Settings → RADIUS Service configuration:
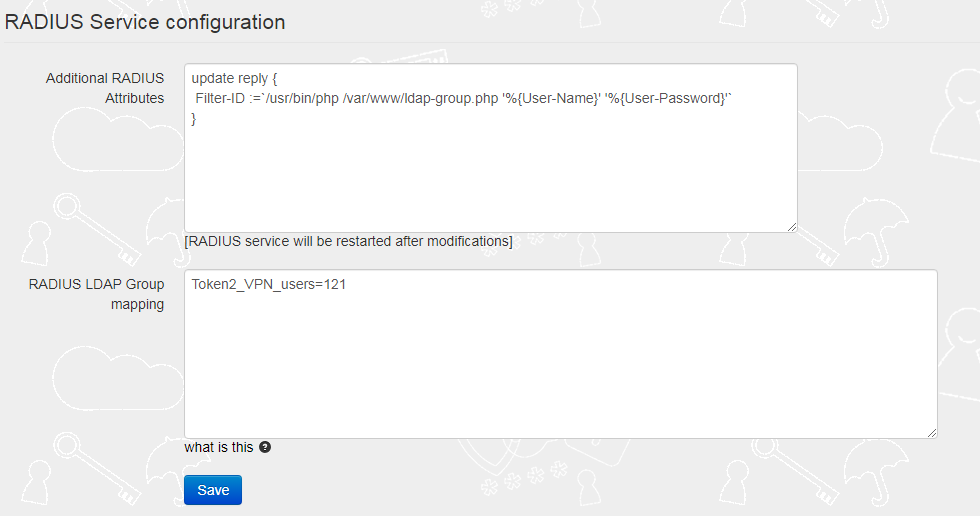
The 'Additional RADIUS Attributes' field should contain the reference to the ldap-group script as shown on the example below:
update reply { Filter-ID :=`/usr/bin/php /var/www/ldap-group.php '%{User-Name}' '%{User-Password}'` }
Important: The group names used for this parameter should not contain "=" sign.
The 'RADIUS LDAP Group mapping' field should contain a mapping rule, which allows members of the specified AD group to have Tunnel-Private-Group-ID attribute equal to some value.
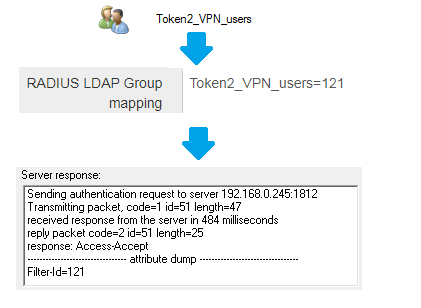
For the example above, if a user belongs to an AD Group named 'Token2_VPN_users', the Filter-ID will be included in the Radius reply as below:
About
Installation and configuration
- Installation and initial configuration
- Network configuration
- Migrating from older versions
- LDAP Configuration
- Azure AD Configuration
- Self-service enrollment portal
- Web and LDAPS Certificates
- Syslog configuration
- Single-factor authentication exceptions
- Slave appliance mode
- Dynamic RADIUS Attributes
Integration guides
Blog
05-03-2026
Introducing TOTPVault — self-hosted TOTP management for teams
 Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
Most TOTP apps work by distributing copies of the secret to every person who needs access — fine for personal accounts, but for shared service accounts it means MFA secrets scattered across people's phones with no clean way to revoke access when someone leaves.
21-12-2025
Android, NFC, and the Missing Piece of WebAuthn
 For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
For years, Android users have faced a frustrating limitation—Android does not support CTAP2 over NFC. This means no PIN verification and no discoverable credentials (passkeys) when using NFC, and therefore limited to simple U2F-style flows without user verification. That said, there finally seems to be a solution.
19-12-2025
Streamline Token2 Classic Tokens in Okta
 Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
Token2 classic hardware tokens provide phishing-resistant multi-factor authentication for your Okta environment. Our updated integration guide shows you how to deploy them using Okta's Custom OTP authenticator method.
