What is multi-factor authentification?
Multi-factor authentification (sometimes referred as two-factor authentication) is currently one of the de-facto standards for systems requiring strong security. In most of the cases, multi-factor authentication is rather complex and not very user-friendly, as it requires additional steps as far as end-users are concerned: e.g. with two-factor authentication, in addition to entering a username and a password (usually considered as a first factor), users need to manually enter an additional code (second factor) that they either receive by text messages, look up in a previously printed list of passwords or generated by a hardware or software token.The basic idea behind multi-factor authentication is that even if thieves manage to phish or steal your password, they still cannot log in to your account unless they also hack or possess that second factor. However, it the method the second factor is delivered to end-users is also important.
For example, using SMS and automated phone calls to receive a one-time token is still considered an MFA and is much more user-friendly than relying on a software token app like Google Authenticator or Token2 Mobile OTP. However, being easier these methods are also less secure. That’s because thieves can intercept that one-time code by tricking your mobile provider into either swapping your mobile device’s SIM card or “porting” your mobile number to a different device. However, if the only 2FA options offered by a site you frequent are SMS and/or phone calls, it is still better than simply relying on a password.
MFA methods
TOTP Algorithm
Theory of TOTP
The idea of using one-time passwords was formulated back in 1981 by Lamport. In principle, OTP can be generated in different ways, but the majority of existing classic as well as modern MFA systems rely on RFC-based TOTP standard. In this article we will give a brief overview of the theoretical background of OTP generation methods this standard uses.
The Time-based One Time Password Algorithm (TOTP) presents a type of key-derivation function that takes a single secret (such as a password or passphrase) as an input and produces a single key as an output. TOTP is a variation of HOTP algorithm, however, with TOTP, the key is dependent on the secret as well as on the current time, instead of an arbitrary counter value defined in HOTP; so current epoch time is considered a counter instead and is calculated as shown in equation below where T0 is a predetermined epoch relative to which all times are counted and Ts is a time step. Time steps used in the majority of TOTP implementations are 30 or 60 seconds.
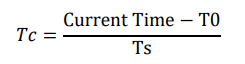
Once the value of the time counter is calculated, the TOTP output can be calculated by signing the master secret (K) and the time counter (Tc) using HMAC function as shown below:
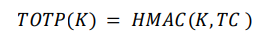
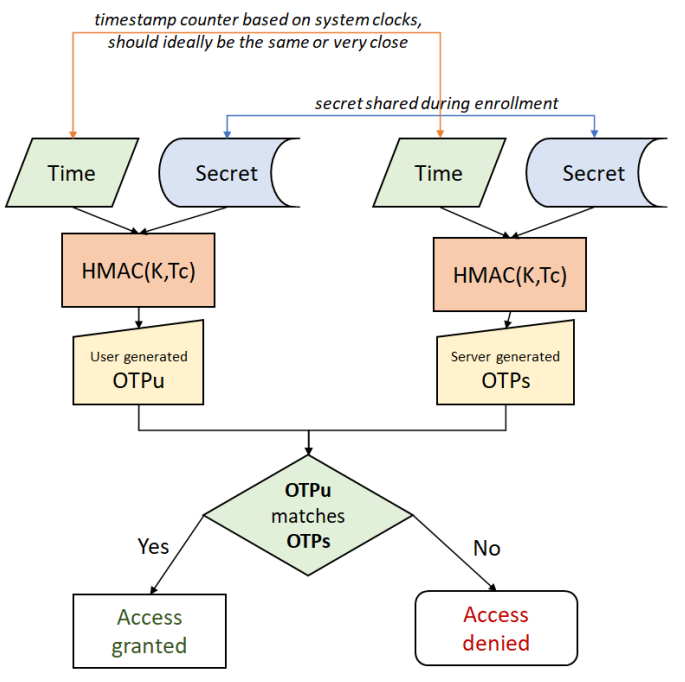
The master secret (K) used to calculate the HMAC hash is also called a shared secret. The reason for that is because this key is shared between the authentication server and the client generating OTP codes. The secret is shared during the registration. So, the values used to generate TOTP are exactly the same at both parties (client and the server): the secret is the same and the time counter used is based on system clocks, ideally the same or within the 30/60 seconds offset. So, as shown in figure below, the validation process of user submitted OTP codes (OTPu) is as simple as comparing with server generated OTP codes (OTPs).
TOTP Implementations
Multifactor authentication using carried devices (a hardware token or an application on a mobile device) as a context was among the first implementations of strong security. The idea behind both types of the devices is simple - they have a source of current time which is used as a counter to calculate the OTP using the shared secret.
Mobile Apps
There are many TOTP-compliant apps, the following are only the most popular examples:- Google Authenticator
- Microsoft Authenticator
- FreeOTP
- Token2 TOTP+
Hardware tokens
We produce and sell many type of different TOTP hardware tokens with different set of features. The list below contains the most popular hardware token categories available with Token2:
FIDO2 Security Keys
FIDO2 is a set of open standards for secure authentication that provides a simpler and stronger alternative to passwords. The standards are developed by the FIDO (Fast IDentity Online) Alliance, a non-profit organization that aims to improve online security by making it easier for people to use strong, unique authentication credentials for their online accounts. FIDO2 consists of two main parts: WebAuthn and CTAP. WebAuthn is a web-based standard that allows websites to use strong authentication methods, such as biometric data (e.g. fingerprints or facial recognition) or security keys, to verify the identity of users. CTAP (Client-to-Authenticator Protocol) is a set of protocols that enable the use of external authentication devices, such as security keys or smartphones, to provide a second factor of authentication. Overall, FIDO2 is a convenient and secure way to protect your online accounts by using strong authentication methods instead of weak and easily compromised passwords.
Algorithms
FIDO2 uses a variety of algorithms to provide strong and secure authentication. The specific algorithms used depend on the type of authentication method being used. For example, biometric authentication methods, such as fingerprint or facial recognition, use pattern recognition algorithms to match the biometric data with the stored template. WebAuthn, one of the main components of FIDO2, uses public-key cryptography to provide secure authentication. In this method, a user's device generates a pair of cryptographic keys (a public key and a private key) and sends the public key to the website. The website then uses this key to verify the user's identity. The private key remains on the user's device and is never shared with the website, ensuring that only the user has access to it. Additionally, FIDO2 uses various protocols and data formats to facilitate secure communication between the website and the user's device. For example, CTAP (Client-to-Authenticator Protocol) defines the communication between the user's device and the external authenticator (e.g. security key or smartphone), while the JSON Web Token (JWT) format is used to encode the authentication data in a secure and interoperable way.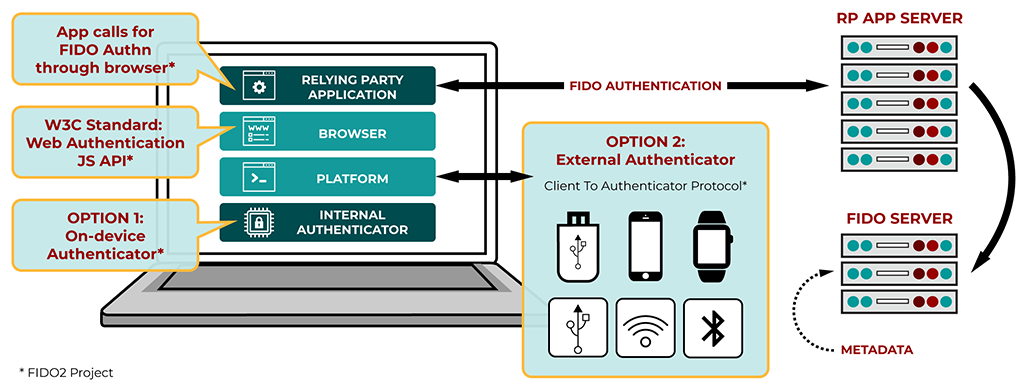
TOTP vs FIDO2
While TOTP provides an extra layer of security by requiring a second factor of authentication, it is not as secure as FIDO2 for several reasons. First, TOTP relies on the user receiving the one-time password via a potentially insecure channel (e.g. a mobile app, which may contain malware), which could be intercepted by an attacker. FIDO2, on the other hand, uses strong authentication methods that are stored on the user's device and are not vulnerable to interception.
Second, TOTP uses a shared secret key that is generated by the website and sent to the user's device. This means that if an attacker were to gain access to the secret key, they could potentially generate valid one-time passwords and gain access to the user's account. FIDO2, on the other hand, uses public-key cryptography, where the private key is never shared with the website and is stored only on the user's device. This makes it much more difficult for an attacker to gain access to the user's account, even if they were to obtain the public key.
Overall, FIDO2 provides a stronger and more secure form of two-factor authentication than TOTP, making it a better choice for protecting sensitive online accounts.
Token2 is a member of FIDO Alliance, and we produce and sell FIDO2 Keys certified by the alliance.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
