Token2 hardware tokens for two-factor authentication with Palo Alto NGFW
 Palo Alto Networks Next-Generation Firewalls (NGFW) give security teams complete visibility and control over all networks using powerful traffic identification,
Palo Alto Networks Next-Generation Firewalls (NGFW) give security teams complete visibility and control over all networks using powerful traffic identification, malware prevention, and threat intelligence technologies.
Multi-factor authentication with PaloAlto NGFW can be implemented using MFA Vendors such as Duo v2,Okta Adaptive and PingID. Fortunately, PaloAlto allows using external RADIUS servers as the authentication source and this will allow implementing two-factor authentication using Token2 TOTPRadius appliance as a more cost-effective alternative to the standard method.
TOTPRadius comes with 5 free user licenses, so if you intend to use 2FA with a mobile app, you can implement the solution at no additional cost. More licenses can be purchased online. Feel free to contact us if you need more than 1000 licenses - volume discounts are available.
In this guide, we will show how to configure a PaloAlto NGFW to work with TOTPRadius in LDAP proxy mode. The authentication will use the standard login forms (username+password only) and the password field is expected to have the LDAP password followed by 6 digit OTP as a single string. For simplicity, this guide will show configuring accounts to use with GlobalProtect VPN.
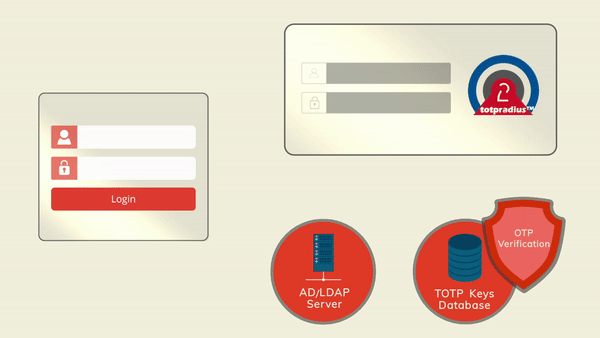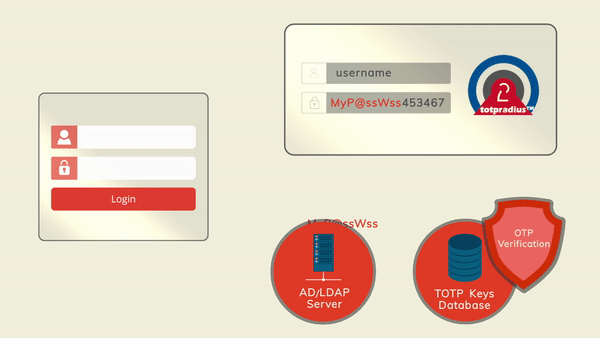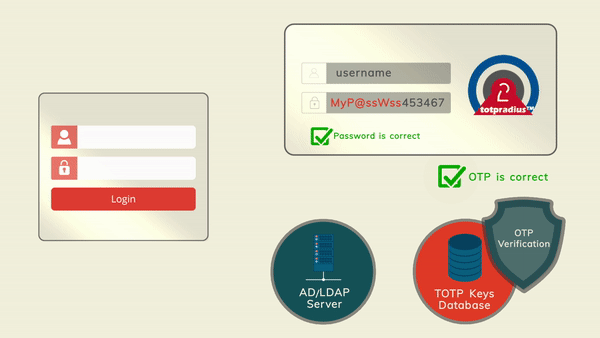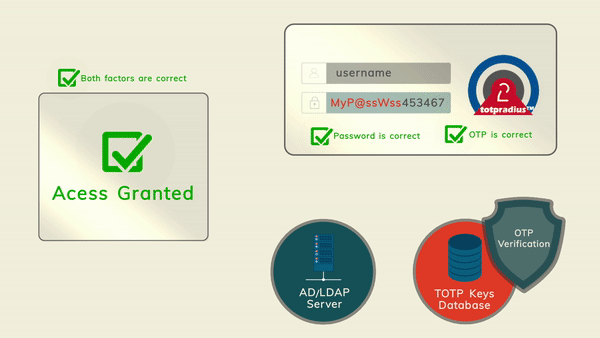
The principle behind LDAP proxy feature of TOTPRadus is that users will provide their AD or LDAP password together with the one-time passwords in the password field.
TOTPRadius will then parse the password, split it into two parts and authenticate the OTP and if correct will send the AD/LDAP password part further to the AD/LDAP server configuration.
This setup was tested only with Microsoft Active Directory as the LDAP backend.
The setup described in this guide is based on the following components:
• PaloAlto NGFW deployed as a virtual appliance on Vmware ESXi (PA VM-100) with preconfigured GlobalProtect Gateway and GlobalProtect Portal configurations• Token2 TOTPRadius 0.2.8 with built-in free 5 users license
• A mobile application (such as Google Authenticator) and/or a classic or a programmable Token2 TOTP hardware token used as the second factor
Step 1. Create a new RADIUS server profile
Navigate to 'Device'(1) on the top menu . Click on the 'RADIUS' button(2) on the left menu and then Click '+Add(3)':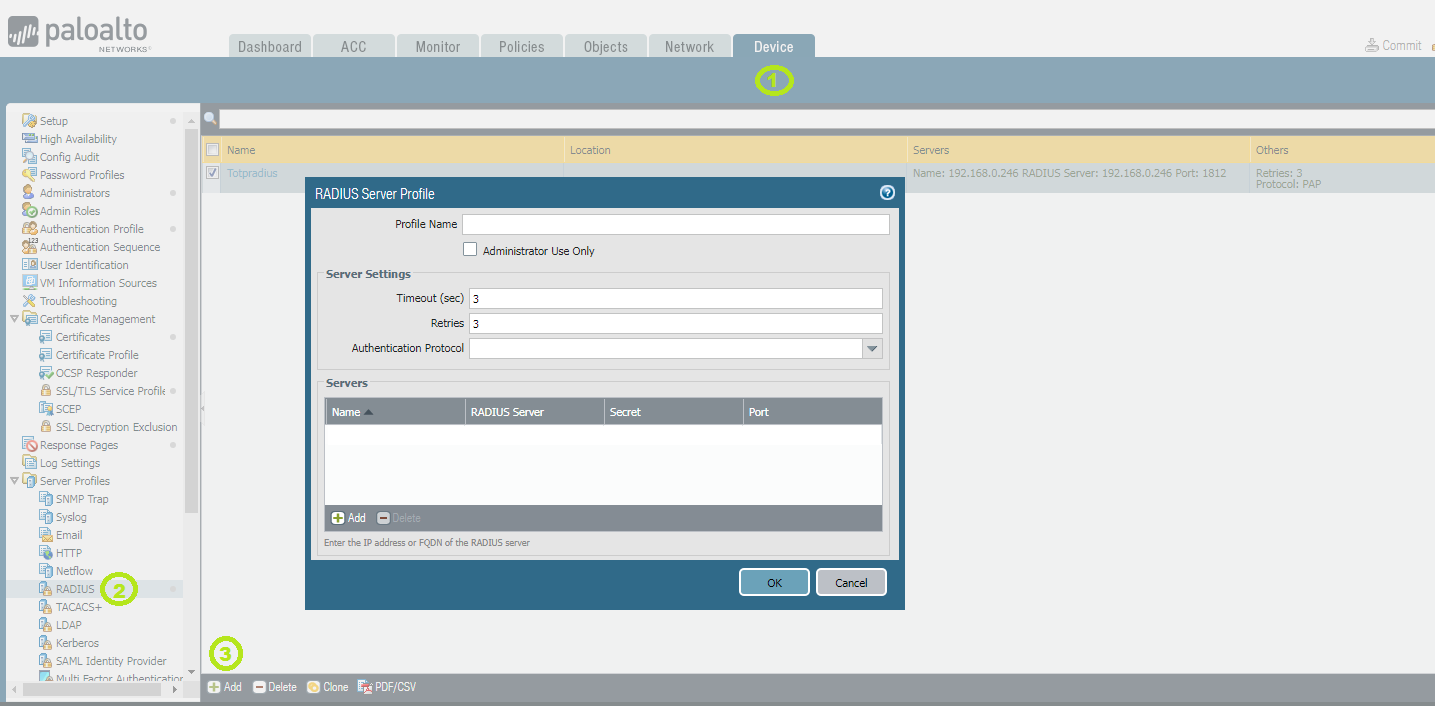
Profile Name: the name of the appliance (we will use 'Totpadius' for this guide as an example)
Authentication Protocol: PAP
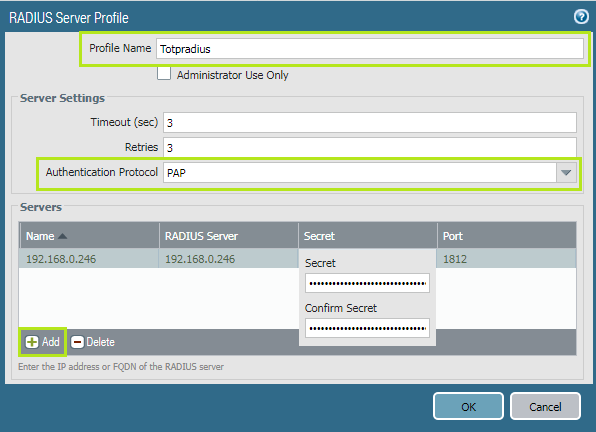
Navigate to Servers tab and click on the '+ Add' button. Provide the following information:
Name: Name of Totpradius server(can be used any name)
RADIUS Server: The IP address or FQDN of the RADIUS server
Secret: The radius secret key of Totpradius. You can find it in Main Settings section of Totpradius appliance
Port: 1812 (by default)
Click 'OK' to complete the process.
Do not forget to commit changes:
Step 2. Add the previously created RADIUS profile to GlobalProtect Gateway Configuration(GlobalProtect Portal Configuration) for Client Authentication
Navigate to 'Network'(1) on the top menu . Click on the 'Gateways' button(2) on the left menu and then click on Gateway's name(3):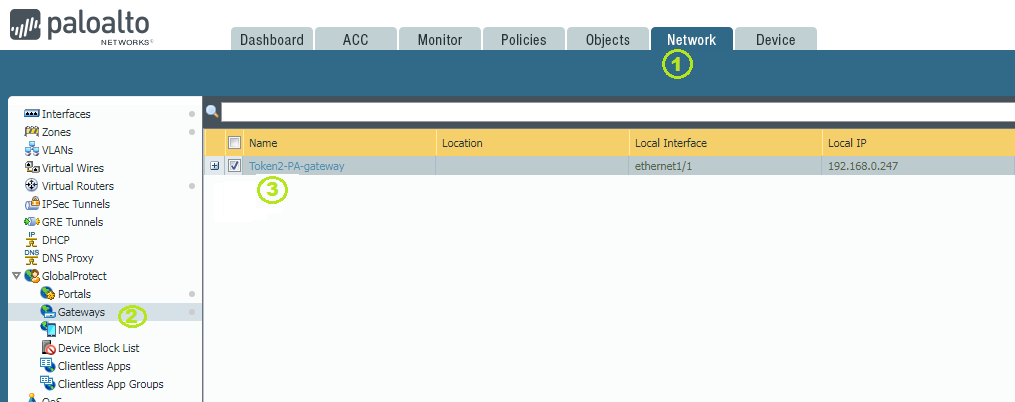
This will open the GlobalProtect Gateway Configuration:
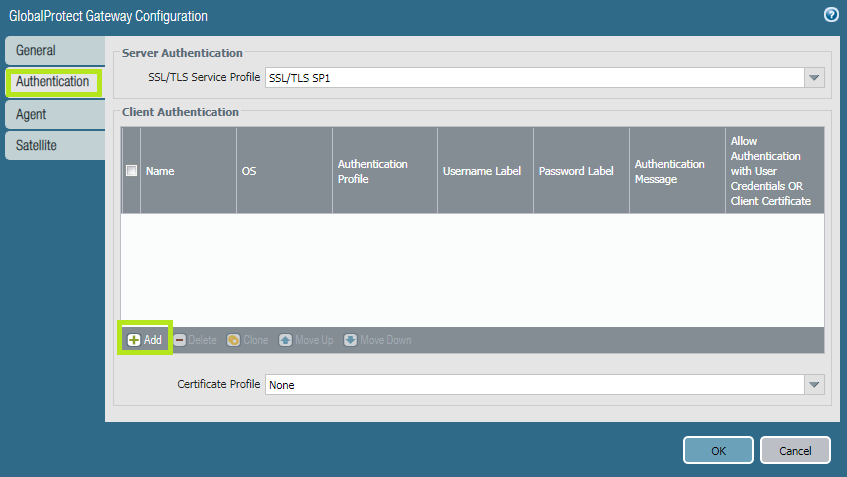
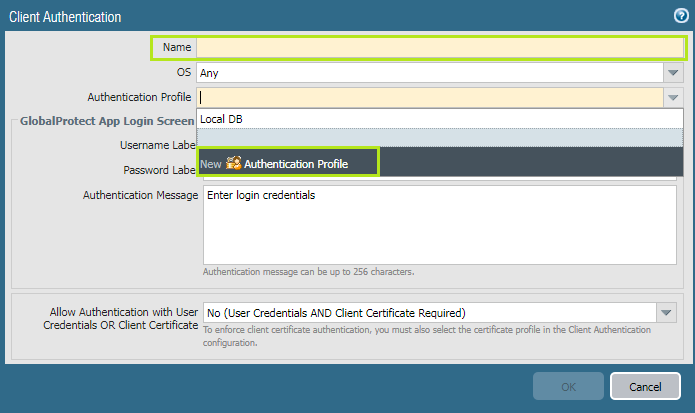
Click 'Authentication' , then '+Add' button. Fill Name value and then in Authentication Profile, select 'New Authentication Profile' from drop-down list:
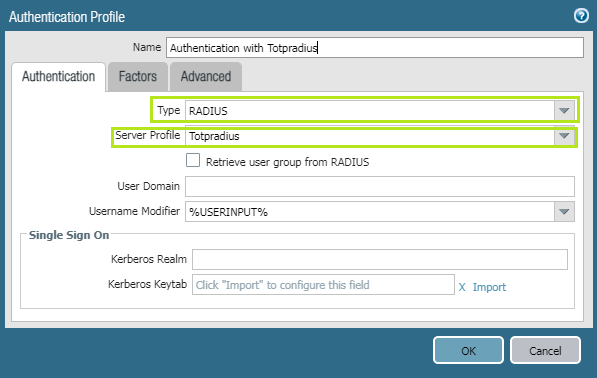
In theAuthentication tab , select Radius Type from the drop-down list . After this, there will appear Server Profile option and you could select RADIUS server profile created on Step 1.
Click 'OK' to complete the process.
Then Click 'OK' again.
Repeat the same steps to configure GlobalProtect Portal Client Authentication.
Step 3. Configure TOTPRadius in LDAP Proxy mode
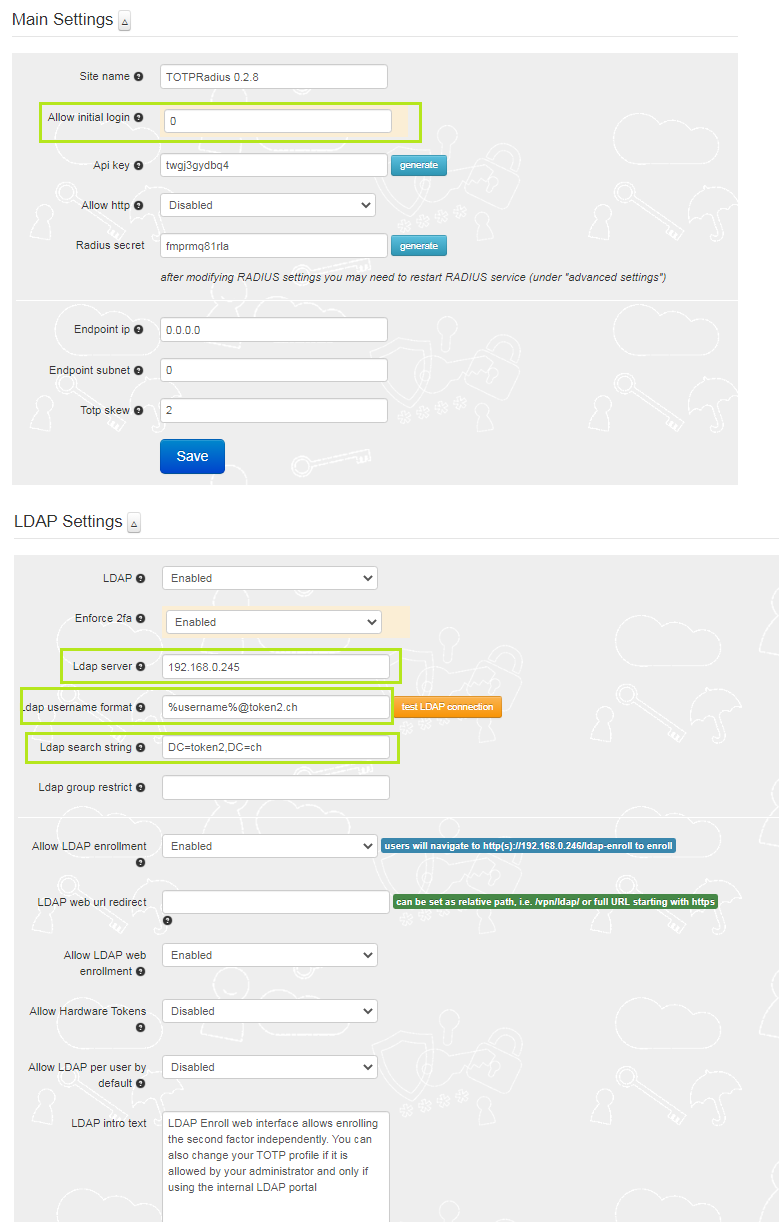
• Set 'Allow initial login' to 0• in LDAP settings section:
• Set LDAP server (hostname or IP for regular LDAP and ldaps://ip_or_hostname for LDAPS). Separate multiple servers with spaces
• Put your NETBIOS prefix or UPN suffix in the username format field keeping %username% string. I.e. if a user in your AD environment is using jsmith@domain.com to log in, the username format field should be set as "%username%@domain.com"
• You also need to define LDAP search string to allow the LDAP connection session to locate the users' OU (i.e. 'ou=users,o=myorgname')
• If you need the user to self-enrol the second factor, enable "Allow LDAP Enrollment" option
Step 4. Generate or set the second factor for the user on TOTPRadius appliance
In this step, we will create a second-factor record (TOTP secret) for LDAP user.Login to TOTPRadius admin interface,go to Users menu and click on New User button. Fill ldap username and click Register .
This will generate a QR code that should be used to provision the TOTP profile on a mobile authenticator app (Google Authenticator, Microsoft Authenticator, Token2 TOTP+ or any other RFC6238-compliant application).
If a hardware token is to be used for this user, click on Edit profile or assign hardware token button and paste the secret key of the hardware token in Token key field in base32 format.
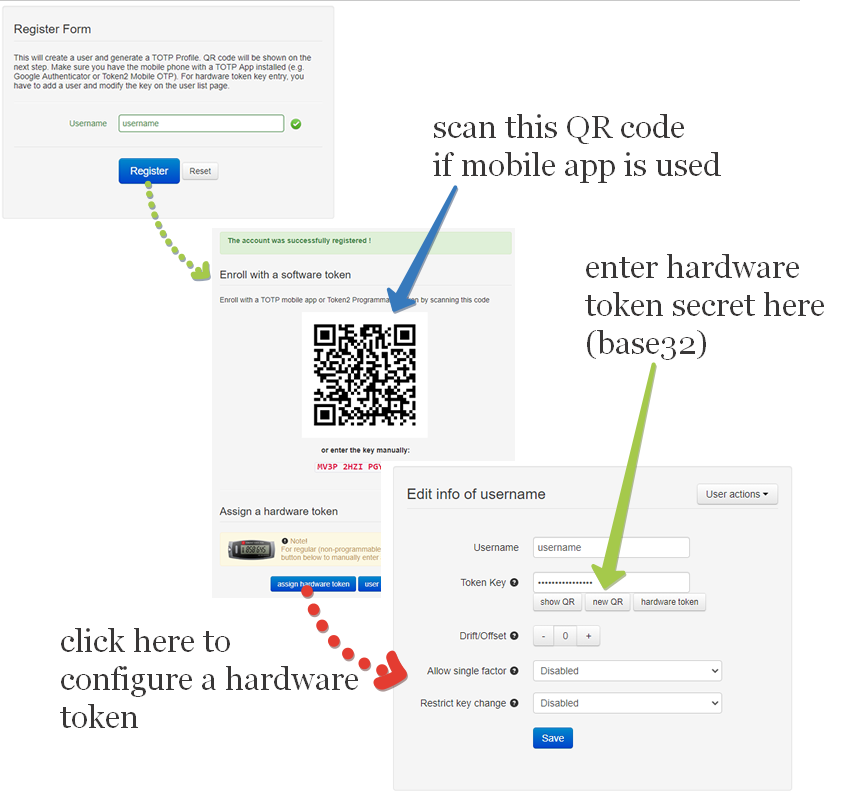
If a programmable hardware token is used, you can burn the secret onto the hardware token by scanning the QR
code using one of the NFC Burner apps.
Ready to connect
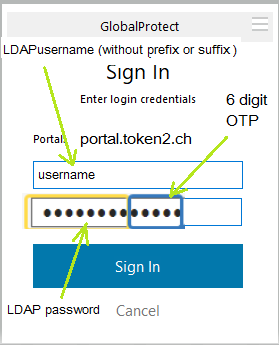
After all 4 steps above are completed successfully and without errors, the user can connect via Global Protect client using his/her username
and active directory password and the 6 digit OTP generated by the hardware token or the mobile app.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
