How to transfer TOTP profiles from Google Authenticator to a Token2 hardware token
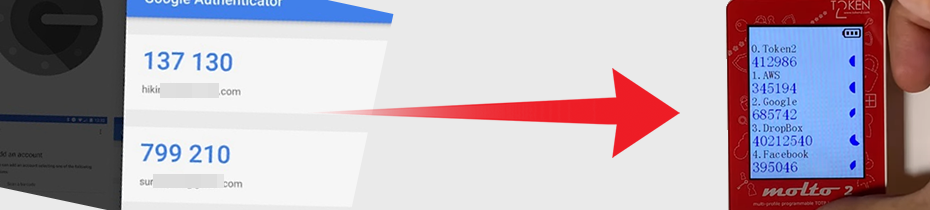
Google Authenticator is still the most popular TOTP application used for 2FA. The accounts in Google Authenticator do not get synced via the cloud as it uses local storage only to save the seeds for TOTP profiles. For this reason, there was no simple way to transfer the accounts to a new device if your phone is running a regular (not rooted) operating system. Around a year ago, Google has updated the app, and it is now possible to manually export the accounts and import them to another phone.
In this guide, we will show how you can benefit from this feature and transfer the accounts to a hardware token. You can use this both for backing up your TOTP profiles and transferring them completely to a hardware token.
A special tool will be required to convert the Google Authenticator's export file to formats possible to be uploaded or burnt to Token2 hardware tokens.
Requirements
You will need the following to perform the migration:
- The latest version of Google Authenticator (older versions do not have the Export feature)
- One of the versions of Token2 Migration Toolset (available as a python script, a portable application, console command, and online service)
- A Token2 hardware token, multi- or single profile (with single-profile hardware token you will need one token per TOTP profile exported from Google Authenticator)
- A device capable of running one of the hardware token provisioning tools (NFC Burner or USB-Config tool)
Step 1. Export profiles from Google Authenticator
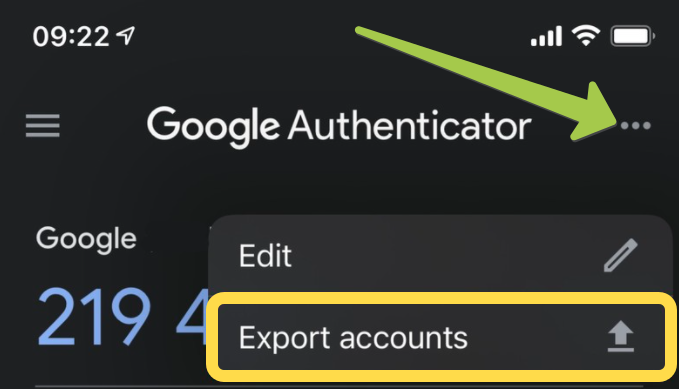
Launch Google Authenticator, tap on the three dots in the upper right-hand corner of the screen and select Export.
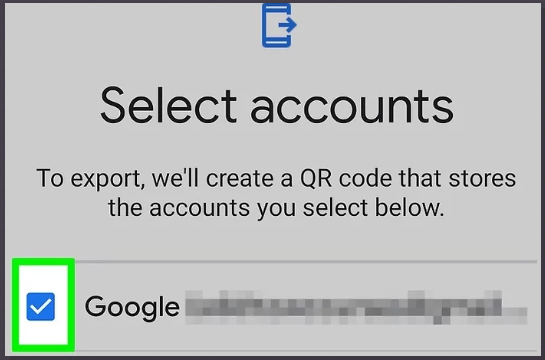
Select up to 10 accounts to export (you can select more than 10, but then multiple QR code images will have to be exported). Tap on Export, then Next once you’ve made your choice.
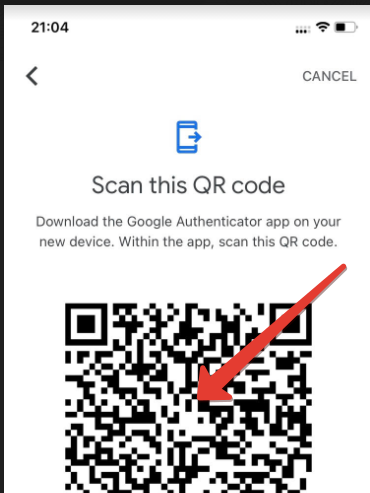
The process will generate one or more QR code images (10 accounts per QR code). Take a screenshot of each QR code and transfer it to the device you will use for Step 2.
Step 2. Convert migration QR images
Launch one of the versions of Token2 Migration Toolset. In this guide, we will use the portable app version in GUI mode, but the process is similar for other versions as well.
Start _GUI-Start.exe and select the QR code image in the first field - click on 'browse' next to 'Input (QR Screenshot)' field. 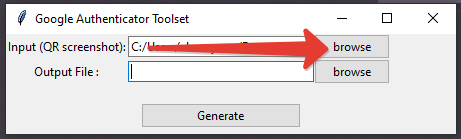
Then, click on 'browse' next to 'Output' field and specify the file name and format.
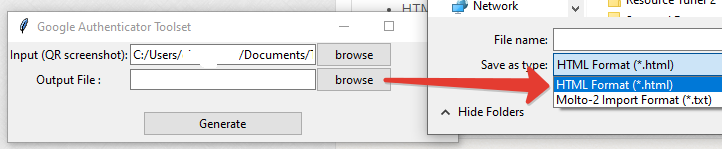
You can select one of the 2 file types:
- HTML : This will generate the list of TOTP profiles containing the seeds in QR format as well as in base32 text. Use this format if you plan to transfer profiles to Token2 hardware tokens using NFC Burner app or to other TOTP Apps
- Molto-2 Import file : Use this format if you plan to transfer all profiles to Token2 Molto-2 hardware token
For this guide, we will use html format as an example.
Click on Generate button to start the process. Please note that this process may take some time. During the process, the window will show the names of TOTP profiles converted. When done, the following message will be shown in the console window:
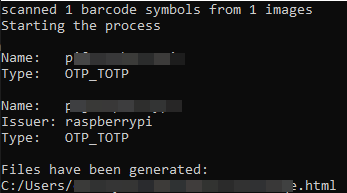
"Files have been generated:" following by the full path of the file. This file will be used to provision the tokens in the next step.
Step 3. Provisioning Token2 hardware token
The files generated in the previous step can be used to provision Token2 hardware tokens. With Molto-2 Import files it is as easy as specifying the file path and clicking on 'bulk import' button on the Molto-2 UBS-Config tool. For all other use cases (burning Token2 hardware tokens via NFC or transferring to alternative TOTP apps) the html format has to be used. The process is reviewed below.
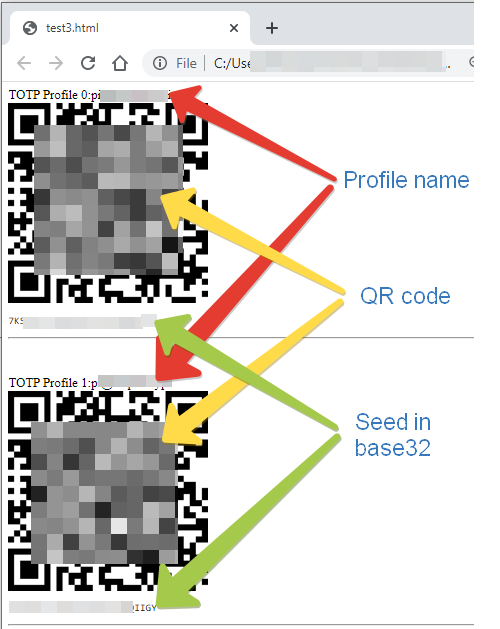
Open the html file generated by the migration toolset. It lists the exported TOTP profiles one by one and each profile is presented in the following format:
- profile title, including the account name and issuer
- QR code (this will be used to provision the hardware tokens in our example)
- Text version of the seed in base32 format
We will use Token2 NFC Burner app for Android to illustrate the process. The process is similar when using apps on the other platforms.
Install Token2 NFC Burner app on your Android device if you have not already done so. Make sure the correct app is installed - there is a separate app for each category of the devices. You can use this page to find which app is needed for your device (choose your model and the platform, you will get the app guides or links on the right column). The Android app we will be using for this example, for miniOTP-2 model, is this one.
Open the Token2 Burner app on your mobile device and click the button to scan a QR code, or manually enter the authentication key (base32 format is to be used). To scan the code, point your device's camera at the QR code of the corresponding TOTP profile in the html file.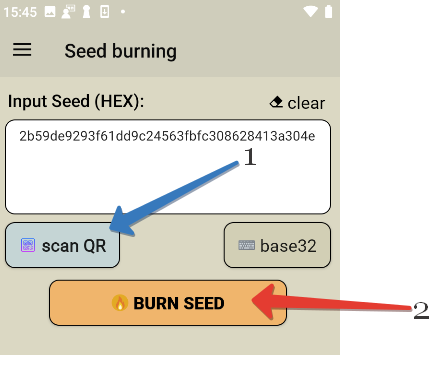
Once the seed field has been filled, touch the "Burn seed" button, then turn the hardware token on and touch the top of the device. The process completion (or any errors) will be shown in the 'Results' area.
Repeat the process for other TOTP profiles listed in the html file, if needed.
Download the migration toolset
The toolset is available in the following versions:
- Open Source Python script, both for Linux and Windows
Migration toolset project on Github - A portable app for Windows (with GUI and command line options). The GUI version was already described abov, the syntax for the command line version is as shown below:
extract_otp_secret_keys.exe --fromimg png_file --moltofile txt_file [--htmlfile html_file ]
where
--fromimg : provides the path of the image file containing the screenshot of QR from Google Authenticator export
--moltofile : saves extracted data in a format compatible with Molto-2 bulk import
--htmlfile : saves extracted data in a html file with QR codes for enrolling TOTP profiles to other apps or Token2 hardware tokens using NFC Burner apps
The app can be downloaded below. Please note that this is the same python script converted to exe format using py2exe, it is known to have performance issues. It is always recommended to use the python version directly.
Download Migration toolset portable app
- The toolset also exists in an online service version. The process is as easy as uploading the export QR image
Migration toolset - Online Service
FAQ
Q: How secure is the process?
The process itself contains 2 different parts - exporting from the app and importing to our solution. The exporting part is designed by Google and is declared secure, see the quote from them below:
We ensured that no data is sent to Google’s servers during the transfer -- communication is directly between your two devices. Your 2SV secrets can’t be accessed without having physical access to your phone and the ability to unlock it.
From our side, we also ensured the security is at the highest level. You can also use the open-source version of the tool, which is less user-friendly, but the code can be easily verified for security.
Q: Why there are 3 versions of the toolset?
All three are based on the same Python script. The online service and desktop app were developed only to simplify the process for those that are not able to install Python and its additional components on their machines.
Subscribe to our mailing list
Want to keep up-to-date with the latest Token2 news, projects and events? Join our mailing list!
